Configuration Analysis
This section includes several views of configuration issues that were detected from scanning the entire virtual infrastructure and by analyzing the configuration settings. Each view provides the capability to Export (at the top-right of the screen) the issues shown in the table. You also have the option to include affected objects which will output each affected object and the objects’ findings values. n
Click on the Analyze now button to initiate a scan and perform an analysis of all configuration data in your virtual infrastructure. It is recommended that you enable and configure automated scheduled scans – see Automatic scheduler. For more information about the Analyze now button, please check section Connect to a System and Analyze).
KB Articles
This view lists all detected issues within the scanned virtual infrastructure that were derived from VMware Knowledge Base articles.
Best Practices
This view includes industry best practices related to VMware’s recommendations. Each best practice is checked against the configuration items from the scanned virtual infrastructure. If a specific best practice is followed for all related objects, the best practice item is marked as Passed. If it is not followed for at least one of the affected objects, then it is marked as Failed. Expanding the best practice section will show details on affected objects and provide the settings that do not align with the best practice.
Vulnerabilities
Runecast Analyzer is constantly updated to detect the latest vulnerabilities for the supported technologies. This section is dedicated to highlight any applicable vulnerability for all your connected systems. A related widget which is located on the main dashboard is providing a quick overview of your vulnerability exposure.
Security Compliance
This section contains security and compliance policies related to VMware’s guidelines, DISA STIG, PCI DSS, HIPAA, BSI IT-Grundschutz, CIS, NIST, GDPR, ISO 27001, Cyber Essentials, Essential Eight, KVKK, CISA, TISAX, and DORA.
VMware SCG
The security rules displayed in this view are taken from the official VMware Security Hardening guides. Their severity differs based on the type of security check:
-
Low Severity: Security hardening that is intended for highly secure environments only.
-
Medium Severity: Security hardening that relates to common environments.
-
Major Severity: Security hardening that can relate to any environment and is related to a host or a network configuration item.
Regardless of the original severity, some security rules may not be required for your organization’s security policy. You might need to customize the displayed security checks by filtering those that are not included in your organization’s security policy. For more information, see Filters.
Analysis results can display the following states:
-
Failed: will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. No Manual check is involved.
-
Passed: will be displayed in case that no object is found to be non-compliant. No Manual check is involved.
-
Not answered: An answer to Manual check is required.
-
Failed (A): will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. A Manual check is involved.
-
Passed (A): will be displayed where no object is found to be non-compliant. A Manual check is involved.
DISA STIG
The security rules displayed in this view are taken from the official Information Assurance Support Environment (IASE) website. Their severity differs based on the type of security check:
-
Low Severity: Any vulnerability, the existence of which degrades measures to protect against loss of Confidentiality, Availability, or Integrity.
-
Medium Severity: Any vulnerability, the exploitation of which has a potential to result in loss of Confidentiality, Availability, or Integrity.
-
High Severity: Any vulnerability, the exploitation of which will directly and immediately result in loss of Confidentiality, Availability, or Integrity.
Regardless of the original severity, some security rules may not be required for your organization’s security policy. You might need to customize the displayed security checks by filtering those that are not included in your organization’s security policy. For more information, see Filters.
Analysis results can display the following states:
-
Failed: will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. No Manual check is involved.
-
Passed: will be displayed in case that no object is found to be non-compliant. No Manual check is involved.
-
Not answered: An answer to Manual check is required.
-
Failed (A): will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. A Manual check is involved.
-
Passed (A): will be displayed where no object is found to be non-compliant. A Manual check is involved.
On DISA STIG profile, additional report is available under the Export button. The STIG Checklist export (CKL format) is offering a .zip file which can be imported in the STIG Viewer.
PCI DSS
The requirements and controls cited in the profile are taken from PCI DSS v4.0 (March 2022). The milestones displayed in this view are taken from the PCI DSS Prioritized Approach. The Prioritized Approach provides six security milestones that help merchants and other organizations incrementally protect against the highest risk factors and escalating threats while on the road to PCI DSS compliance. Milestones range from 1-6, with 1 being the highest priority and 6 being the lowest:
-
1: Remove sensitive authentication data and limit data retention. This milestone targets a key area of risk for entities that have been compromised.
-
2: Protect the perimeter, internal, and wireless networks. This milestone targets controls for points of access to most compromises – the network or a wireless access point.
-
3: Secure payment card applications. This milestone targets controls for applications, application processes, and application servers.
-
4: Monitor and control access to your systems. Controls for this milestone allow you to detect the who, what, when, and how concerning and who is accessing your network and cardholder data environment.
-
5: Protect stored cardholder data. For those organizations that have analyzed their business processes and determined that they must store Primary Account Numbers, Milestone Five targets key protections mechanisms for that stored data.
-
6: Finalize remaining compliance efforts and ensure all controls are in place. The intent of Milestone Six is to complete PCI DSS requirements and finalize all remaining related policies, procedures, and processes needed to protect the cardholder data environment.
Regardless of the original severity, some security rules may not be required for your organization’s interpretation of the security policy. You might need to customize the displayed security checks by filtering those that are not required. For more information, see Filters.
PCI DSS contains two types of rules (Customizable and Non-customizable). The main difference between them is that Customizable rules allows the user to change the parameters default values, used by the checks, to the desired ones. Additional filter tab named Customizable can be used to quickly select one of the two types. To change the default values, expand the rule marked as Customizable and navigate to the Customize tab. A short note describing the setting purpose and its default value is available. Click on the Add Custom Value button, insert the custom value on the dedicated field and select an inventory object which will be evaluated against new value. By selecting a parent object, the value will be propagated to its children. After pressing the Save button you will be able to see a new line presenting the object in scope, the custom value, the username and the time when he updated the value. Multiple values can be added to different inventory objects. A value set to children object will rewrite the value set on parent level. After customization is done, don't forget to Analyze the environment so the new values are considered. Each one of the customized rules will be flagged with a C mark in the Result status column.
Every security check can either return a result of Failed or Passed. In cases where there is at least one object in your infrastructure that is not compliant with a specific security check, this check will be marked as Failed. The list of non-compliant objects can be viewed in the details of the affected objects section. A result of Passed means there are no objects failing for the specific check, but this does not mean you are fully compliant against the whole PCI DSS requirement or control.
On PCI DSS profile, additional report is available under the Export button. The Consolidated host report is offering a better overview of all the PCI DSS rules failed or passed for each vCenter, on Cluster and ESXI level.
HIPAA
This profile relates to the Health Insurance Portability and Accountability Act of 1996 (HIPAA) published by the Secretary of the U.S. Department of Health and Human Services (HHS).
Organizations (called "covered entities") must put in place technical safeguards to secure individuals’ "electronic protected health information" (e-PHI). The profile lists relevant technical safeguards in the virtual infrastructure that are automatically checked and compared against the requirements of the HIPAA Security Standards for the Protection of Electronic Protected Health Information (the Security Rule).
Every security check can either return a result of Failed or Passed. In cases where there is at least one object in your infrastructure that is not compliant with a specific security check, this check will be marked as Failed. The list of non-compliant objects can be viewed in the details of the affected objects section. A result of Passed means there are no objects failing for the specific check.
Regardless of the original severity, some security rules may not be required for your organization’s interpretation of the security policy. You might need to customize the displayed security checks by filtering those that are not required. For more information, see Filters.
BSI IT-Grundschutz
IT-Grundschutz - the basis for information security. The IT-Grundschutz developed by the BSI makes it possible to identify and implement necessary security measures through a systematic procedure. The BSI standards provide best practices, the IT-Grundschutz Compendium concrete requirements.
Every security check can either return a result of Failed or Passed. In cases where there is at least one object in your infrastructure that is not compliant with a specific security check, this check will be marked as Failed. The list of non-compliant objects can be viewed in the details of the affected objects section. A result of Passed means there are no objects failing for the specific check.
Regardless of the original severity, some security rules may not be required for your organization’s interpretation of the security policy. You might need to customize the displayed security checks by filtering those that are not required. For more information, see Filters.
BSI C5
The C5, also known as the Cloud Computing Compliance Criteria Catalogue, outlines the basic requirements for secure cloud computing. It is primarily designed to provide a high level of assurance in the security of cloud services. It's based on international standards such as ISO 27001, but it goes beyond these standards by including additional controls specifically tailored for cloud environments.
Every security check can either return a result of Failed or Passed. In cases where there is at least one object in your infrastructure that is not compliant with a specific security check, this check will be marked as Failed. The list of non-compliant objects can be viewed in the details of the affected objects section. A result of Passed means there are no objects failing for the specific check.
Regardless of the original severity, some security rules may not be required for your organization’s interpretation of the security policy. You might need to customize the displayed security checks by filtering those that are not required. For more information, see Filters.
CIS
CIS® (Center for Internet Security, Inc.) is a forward-thinking, non-profit entity that harnesses the power of a global IT community to safeguard private and public organizations against cyber threats.
CIS VMware ESXi Benchmarks are documents intended for system and application administrators, security specialists, auditors, help desk, and platform deployment personnel who plan to develop, deploy, assess, or secure solutions that incorporate VMware ESXi.
The Benchmarks define the following configuration profiles:
-
Level 1 (L1): Corporate/Enterprise Environment (general use)
-
Level 2 (L2): High Security/Sensitive Data Environment (limited functionality)
Analysis results can display the following states:
-
Failed: will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. No Manual check is involved.
-
Passed: will be displayed in case that no object is found to be non-compliant. No Manual check is involved.
-
Not answered: An answer to Manual check is required.
-
Failed (A): will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. A Manual check is involved.
-
Passed (A): will be displayed where no object is found to be non-compliant. A Manual check is involved.
Regardless of the original severity, some security rules may not be required for your organization’s interpretation of the security policy. You might need to customize the displayed security checks by filtering those that are not required. For more information, see Filters.
NIST
The National Institute of Standards and Technology (NIST) was founded in 1901 and is now part of the U.S. Department of Commerce. NIST is one of the nation's oldest physical science laboratories.
From the smart electric power grid and electronic health records to atomic clocks, advanced nanomaterials, and computer chips, innumerable products and services rely in some way on technology, measurement, and standards provided by the National Institute of Standards and Technology.
Today, NIST measurements support the smallest of technologies to the largest and most complex of human-made creations—from nanoscale devices so tiny that tens of thousands can fit on the end of a single human hair up to earthquake-resistant skyscrapers and global communication networks.
The NIST SP 800-53 database represents the security controls and associated assessment procedures defined in NIST SP 800-53 Revision 5 Recommended Security Controls for Information Systems and Organizations.
This recommended sequencing prioritization helps to ensure that the foundational security controls upon which other controls depend are implemented first, thus enabling organizations to deploy controls in a more structured and timely manner in accordance with available resources.
Analysis results can display the following states:
-
Failed: will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. No Manual check is involved.
-
Passed: will be displayed in case that no object is found to be non-compliant. No Manual check is involved.
-
Not answered: An answer to Manual check is required.
-
Failed (A): will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. A Manual check is involved.
-
Passed (A): will be displayed where no object is found to be non-compliant. A Manual check is involved.
Regardless of the original severity, some security rules may not be required for your organization’s interpretation of the security policy. You might need to customize the displayed security checks by filtering those that are not required. For more information, see Filters.
GDPR
The General Data Protection Regulation (GDPR) is a European privacy law intended to harmonize data protection laws throughout the European Union (EU) by applying a single data protection law that is binding throughout each EU member state. GDPR profile focuses on:
-
Data Access: Article 25 of the GDPR states that the controller "shall implement appropriate technical and organizational measures for ensuring that, by default, only personal data which are necessary for each specific purpose of the processing are processed".
-
Data Protection: Article 32 of the GDPR requires that organizations must "implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk, including …the pseudonymization and encryption of personal data…". In addition, organizations must safeguard against the unauthorized disclosure of or access to personal data.
-
Monitoring and Logging: Article 30 of the GDPR states that "each controller and, where applicable, the controller’s representative, shall maintain a record of processing activities under its responsibility".
Analysis results can display the following states:
-
Failed: will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. No Manual check is involved.
-
Passed: will be displayed in case that no object is found to be non-compliant. No Manual check is involved.
-
Not answered: An answer to Manual check is required.
-
Failed (A): will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. A Manual check is involved.
-
Passed (A): will be displayed where no object is found to be non-compliant. A Manual check is involved.
ISO 27001
Published by the International Organization for Standardization (ISO) in partnership with the International Electrotechnical Commission (IEC), the ISO 27001 was developed to help organizations, of any size or any industry, make the information assets they hold more secure. ISO-27001 is part of a set of standards in the ISO/IEC 27000 family.
Analysis results can display the following states:
-
Failed: will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. No Manual check is involved.
-
Passed: will be displayed in case that no object is found to be non-compliant. No Manual check is involved.
-
Not answered: An answer to Manual check is required.
-
Failed (A): will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. A Manual check is involved.
-
Passed (A): will be displayed where no object is found to be non-compliant. A Manual check is involved.
Regardless of the original severity, some security rules may not be required for your organization’s interpretation of the security policy. You might need to customize the displayed security checks by filtering those that are not required. For more information, see Filters.
Cyber Essentials
Cyber Essentials is a United Kingdom government backed scheme that helps organizations adopt good practices in information security.
Analysis results can display the following states:
-
Failed: will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. No Manual check is involved.
-
Passed: will be displayed in case that no object is found to be non-compliant. No Manual check is involved.
-
Not answered: An answer to Manual check is required.
-
Failed (A): will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. A Manual check is involved.
-
Passed (A): will be displayed where no object is found to be non-compliant. A Manual check is involved.
Regardless of the original severity, some security rules may not be required for your organization’s interpretation of the security policy. You might need to customize the displayed security checks by filtering those that are not required. For more information, see Filters.
Essential Eight
The Essential Eight is a series of baseline mitigation strategies defined by the Australian Cyber Security Centre. Implementing these strategies as a minimum makes it much harder for adversaries to compromise systems.
Analysis results can display the following states:
-
Failed: will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. No Manual check is involved.
-
Passed: will be displayed in case that no object is found to be non-compliant. No Manual check is involved.
-
Not answered: An answer to Manual check is required.
-
Failed (A): will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. A Manual check is involved.
-
Passed (A): will be displayed where no object is found to be non-compliant. A Manual check is involved.
Regardless of the original severity, some security rules may not be required for your organization’s interpretation of the security policy. You might need to customize the displayed security checks by filtering those that are not required. For more information, see Filters.
KVKK
The Personal Data Protection Law (Turkish: Kişisel Verilerin Korunması Kanunu, KVKK) is a law in Turkey that regulates personal data protection and outlines the legal obligations that entities and individuals dealing with personal data must comply with. This profile helps your organization comply with the technical requirements for Data Protection, Data Access and Audit readiness. KVKK profile focuses on:
-
Data Access: Article 12.1.b of the KVKK states that the data controller "is obliged to take all necessary technical and organizational measures to provide an appropriate level of security for the purposes of preventing unlawful access to personal data".
-
Data Protection: Article 12.1.c of the KVKK states that the data controller "is obliged to take all necessary technical and organizational measures to provide an appropriate level of security for the purposes of ensuring protection of personal data.".
-
Monitoring and Logging: Article 12.3 of the KVKK states that data the controller "is obliged to carry out the necessary audits, or have them made, in its own institution or organization, in order to ensure the implementation of the provisions of this Law".
Analysis results can display the following states:
-
Failed: will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. No Manual check is involved.
-
Passed: will be displayed in case that no object is found to be non-compliant. No Manual check is involved.
-
Not answered: An answer to Manual check is required.
-
Failed (A): will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. A Manual check is involved.
-
Passed (A): will be displayed where no object is found to be non-compliant. A Manual check is involved.
CISA
Cybersecurity and Infrastructure Security Agency (CISA) is an agency of the United States Department of Homeland Security (DHS) responsible for improving government cybersecurity and protecting infrastructure from private and nation-state hackers. NSA and CISA developed Kubernetes Hardening Guidance in furtherance of their respective cybersecurity missions, including their responsibilities to develop and issue cybersecurity specifications and mitigations.
Analysis results can display the following states:
-
Failed: will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. No Manual check is involved.
-
Passed: will be displayed in case that no object is found to be non-compliant. No Manual check is involved.
-
Not answered: An answer to Manual check is required.
-
Failed (A): will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. A Manual check is involved.
-
Passed (A): will be displayed where no object is found to be non-compliant. A Manual check is involved.
Regardless of the original severity, some security rules may not be required for your organization’s interpretation of the security policy. You might need to customize the displayed security checks by filtering those that are not required. For more information, see Filters.
TISAX
Trusted Information Security Assessment Exchange (TISAX) is a security standard devised by the German Association of the Automotive Industry (VDA) in 2017 to ensure a base level of information & cyber security in the European auto industry. It is administered by the ENX Association and TISAX's Information Security Assessment (ISA) is an information security requirements catalogue based on key aspects of the international standard ISO/IEC 27001.
Analysis results can display the following states:
-
Failed: will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. No Manual check is involved.
-
Passed: will be displayed in case that no object is found to be non-compliant. No Manual check is involved.
-
Not answered: An answer to Manual check is required.
-
Failed (A): will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. A Manual check is involved.
-
Passed (A): will be displayed where no object is found to be non-compliant. A Manual check is involved.
Regardless of the original severity, some security rules may not be required for your organization’s interpretation of the security policy. You might need to customize the displayed security checks by filtering those that are not required. For more information, see Filters.
DORA
The Digital Operational Resilience Act (DORA), is a major piece of European Union legislation (Regulation (EU) 2022/2554) on cybersecurity for financial entities, such as banks or credit institutions.
Analysis results can display the following states:
-
Failed: will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section.
-
Passed: will be displayed in case that no object is found to be non-compliant.
-
Not answered: An answer to Manual check is required.
-
Failed (A): will be displayed where there is at least one object in your infrastructure that is not compliant with a specific security check. The list of non-compliant objects can be viewed in the details of the affected objects section. A Manual check is involved.
-
Passed (A): will be displayed where no object is found to be non-compliant. A Manual check is involved.
DORA contains two types of rules (Customizable and Non-customizable). The main difference between them is that Customizable rules allows the user to change the parameters default values, used by the checks, to the desired ones. Additional filter tab named Customizable can be used to quickly select one of the two types. To change the default values, expand the rule marked as Customizable and navigate to the Customize tab. A short note describing the setting purpose and its default value is available. Click on the Add Custom Value button, insert the custom value on the dedicated field and select an inventory object which will be evaluated against new value. By selecting a parent object, the value will be propagated to its children. After pressing the Save button you will be able to see a new line presenting the object in scope, the custom value, the username and the time when he updated the value. Multiple values can be added to different inventory objects. A value set to children object will rewrite the value set on parent level. After customization is done, don't forget to Analyze the environment so the new values are considered. Each one of the customized rules will be flagged with a C mark in the Result status column.
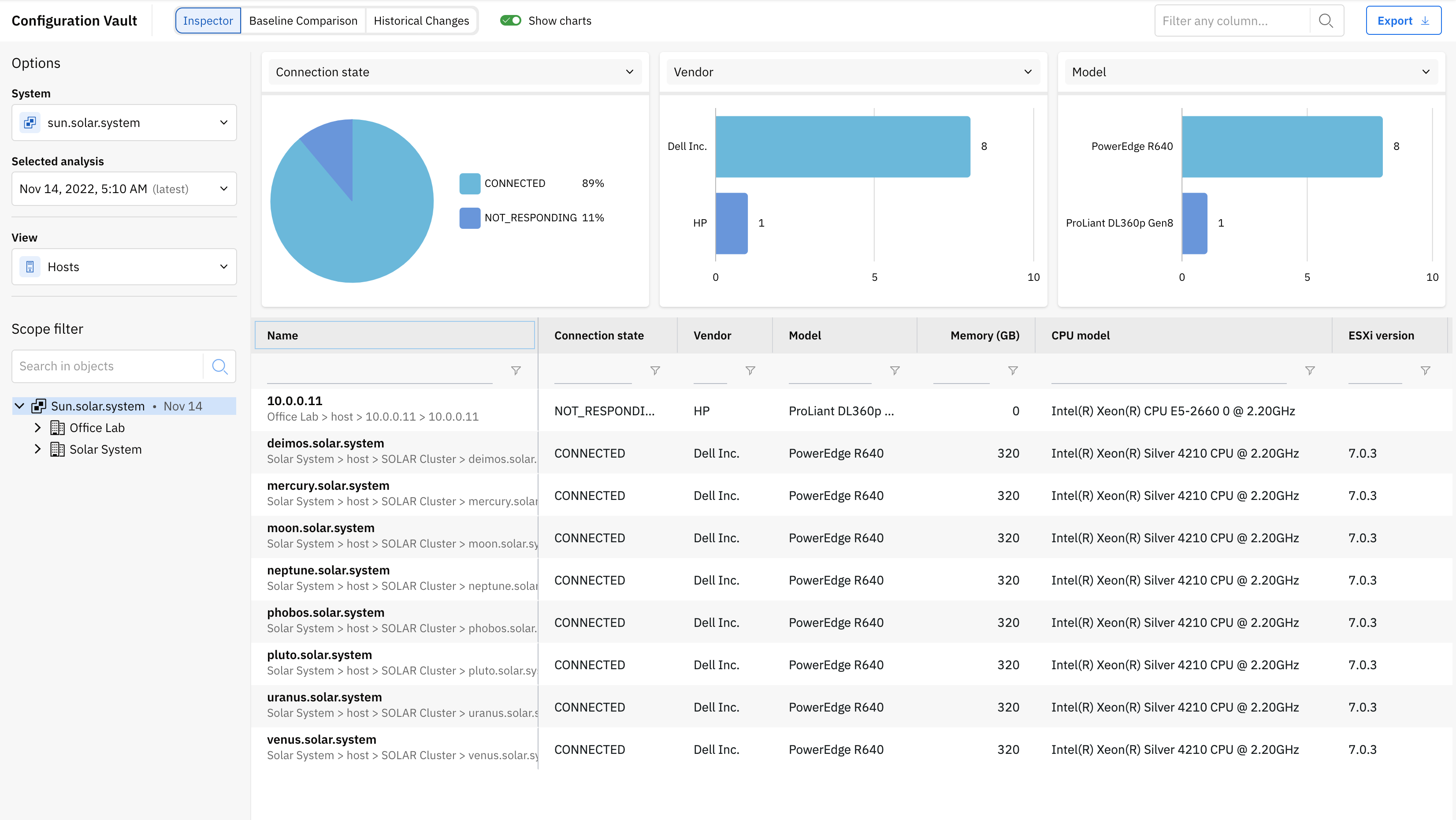
Configuration Vault
Configuration vault allows you to review hardware specifications, settings and parameters for the systems that are added in Runecast Analyzer. You can browse the current configuration, go back in time and also perform configuration drift analysis by switching to the Inspector, Baseline Comparison or Historical changes sub-sections.
From the left panel you can select system, analysis timestamp and specific view - for example ESXi hosts, VMs, AWS EC2 instances, etc. The views are system-specific and define the main focus for the information shown in the main table. You can also set a Scope Filter to select the scope you want to focus on.
Three charts are available for a graphical view of different specifications. You can switch the displayed information using the dropdown button at the top of each chart.
Depending on the selected view and scope from the inventory, all available parameters and specifications are presented in the table. You can expand the size of the table by hiding the charts using the button located in the upper right corner.
By clicking on the object name you'll access its configuration data in a separate modal, keeping your focus on the details you're interested in.
Note
Certain object types from the vSphere system can include also information about the tasks performed on them since the last analysis, but up to 20 entries. The information includes start and end time of the task, its status and initiator.
Scroll to the right side to check all the available columns. Each column of the table offers the possibility to filter various values depending on the displayed parameters. If the value to be displayed is too complex, then the Show button will be returned. Click on it to view the full content. A button to copy to the clipboard is handy on the top left side of the new panel.
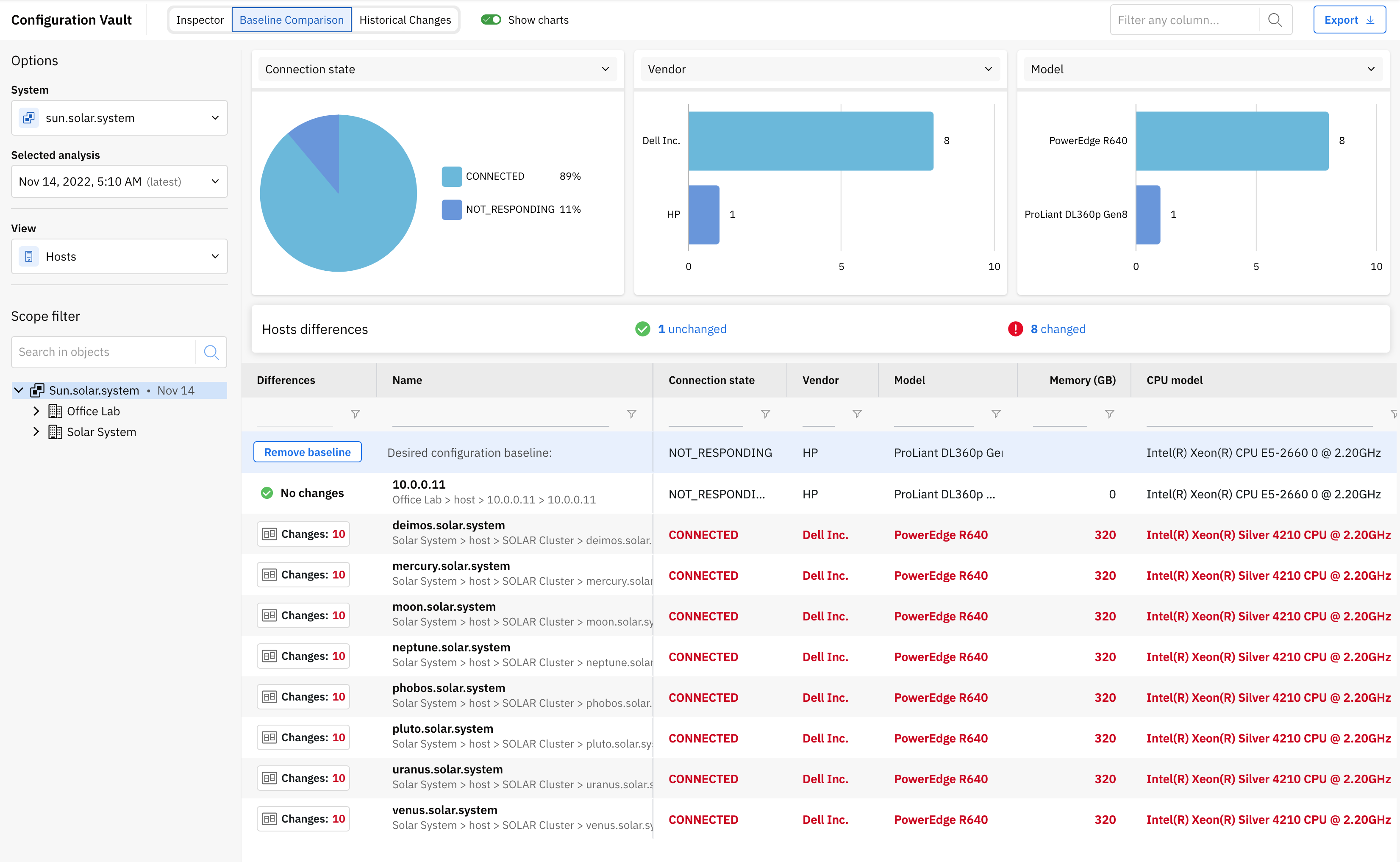
To find the deviations between an object and similar counterparts, just switch to Baseline Comparison section and select the desired inventory item inside the table, thus turning it into a baseline.
A new line containing all available fields of the selected object as a baseline will be revealed in the table. Hovering each one of the values from its columns will offer the possibility to edit or remove it. The new change will be taken into consideration during comparison with the other objects. By default, the object selected as a baseline will present no changes.
The total number of drifts, as well as a detail of them, is displayed in front of each object. Click the Compare button to see them side by side.
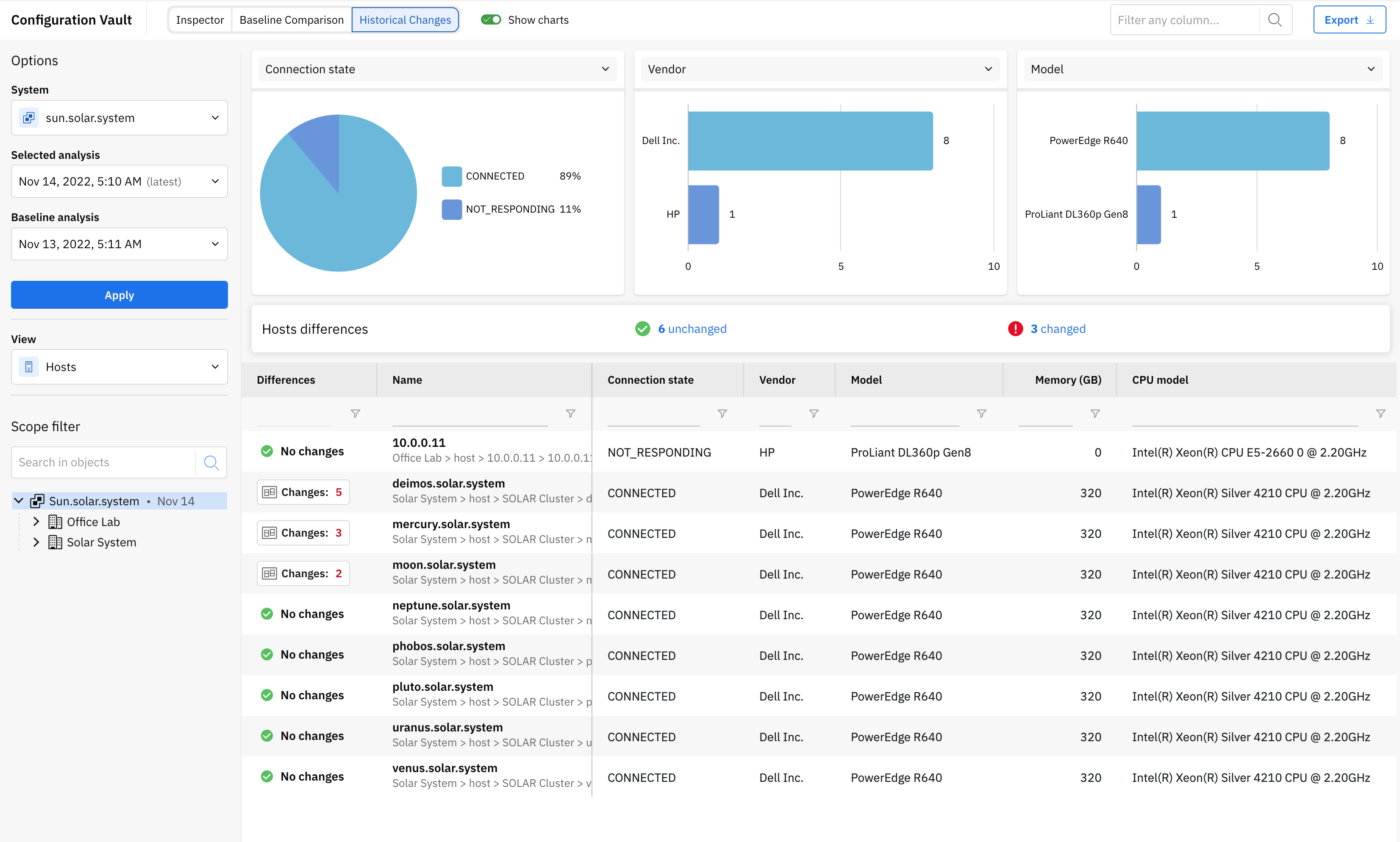
You can also review changes in the configuration between two analyses. To achieve this, navigate to the Historical changes section and select appropriate analyses in the left panel. For supported object types within the vSphere system, the historical drift details will include data about tasks performed between the two selected analyses. The information can be used to correlate configuration changes to actual events performed in your environment.
If you want to get the table data in .csv format, the Export button is located just above it on the right side.
HW Compatibility
In this section, the Analyzer shows you the compliance status of your hardware against VMware Hardware Compatibility List (HCL). Keeping your vSphere hardware aligned with VMware HCL is critical for the health and support of your virtual environment.
Warning
ESXi 6.0 - 8.0 are supported for this feature. Ensure you have the minimum required permissions specified in System Requirements.
The feature is accessed by clicking the HW Compatibility button from the sidebar:
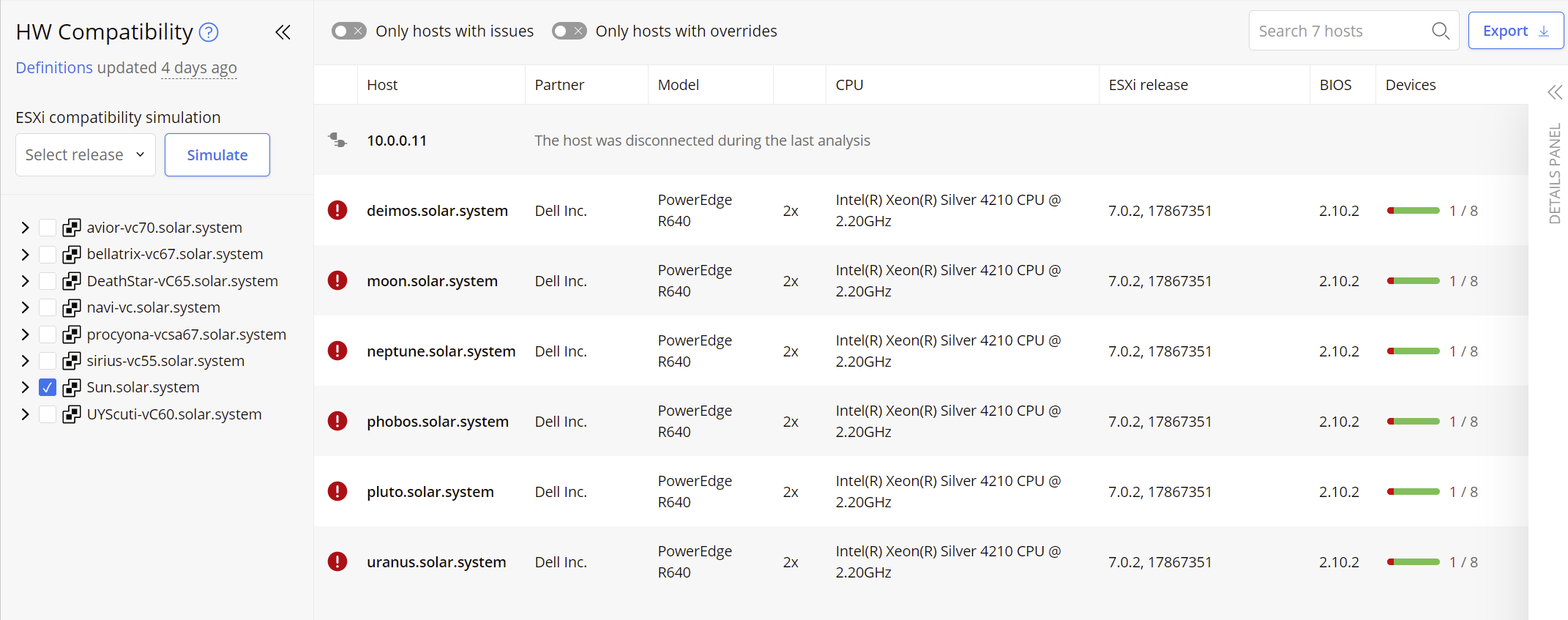
On selection, the Hardware Compatibility Overview screen will be shown in the main panel:
On the left-hand side are available the information about definitions, a compatibility simulator, and an inventory filter.
-
The definitions’ age is presented in hours or days and indicates the time that has elapsed since the last update. The exact day is displayed on hover.
-
The ESXi Compatibility Simulation component is offering the ability to show if your current hardware would have compatibility with other ESXi versions available (6.0 and above), simulating possible upgrade/downgrade based on the version selected. Choose the desired version from the revealed drop-down list. Initiate the compatibility analysis by pressing the Simulate button. The results are displayed on the right-hand side. The icons
 ,
,  or
or 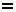 located before the ESXi Release indicate if your selected ESXi version for simulation will be an upgrade or downgrade from the present version. A detailed description of the right-hand side panel is described in the next paragraph. Press Turn off to return to the current version results.
located before the ESXi Release indicate if your selected ESXi version for simulation will be an upgrade or downgrade from the present version. A detailed description of the right-hand side panel is described in the next paragraph. Press Turn off to return to the current version results. -
The inventory filter component provides an inventory tree, showing all vCenter Servers, and includes nested Datacenters and Clusters. This allows you to select appropriate objects as desired. By default, all vCenters monitored by the Analyzer and their licensed hosts are displayed. If you want to focus attention on specific Datacenter(s) or Cluster(s) you can tick the corresponding checkboxes which will filter the view based on your selection.
Note
Hosts that are not part of any cluster are grouped into an area entitled Standalone Hosts.
On the right-hand side all Hosts are presented in a table, offering a breakdown of configuration and the compatibility evaluation. Cross-checks between the Host’s system Data and the HCL industry knowledge will produce an overall state for the host:
-
 Compatible: the Server and all I/O devices were marked as compatible automatically after the evaluation. No override applied.
Compatible: the Server and all I/O devices were marked as compatible automatically after the evaluation. No override applied. -
 Compatible (Override applied): the Server and all I/O devices were marked as compatible after the evaluation. The override functionality was applied to at least one object.
Compatible (Override applied): the Server and all I/O devices were marked as compatible after the evaluation. The override functionality was applied to at least one object. -
 Possibly Incompatible: the Server and all I/O devices were marked as incompatible automatically after the evaluation.
Possibly Incompatible: the Server and all I/O devices were marked as incompatible automatically after the evaluation. -
 Possibly Incompatible (Override applied): the Server and all I/O devices were marked as incompatible after the evaluation. Even if the override functionality was applied at least once, there are still remaining objects which are identified as not compatible.
Possibly Incompatible (Override applied): the Server and all I/O devices were marked as incompatible after the evaluation. Even if the override functionality was applied at least once, there are still remaining objects which are identified as not compatible.
In case of incompatibility, the parameter that contributed to this status will be indicated by the red color.
Optionally, you can switch between views of all Hosts or just those with issues by toggling the Only hosts with issues switch found in the top bar. Similarly, you can switch between all Hosts or those with overrides by toggling the Only hosts with overrides switch.
The option to export the report in .csv format is available by using the Export button.
For each Host, the name, Partner, Model, CPU, ESXi release, BIOS and the number of I/O devices are each displayed in separate columns. By clicking on a row, an additional detail panel will appear providing more data.
The detail panel is divided into tabs which are described in the following sections.
Server
Server tab contains a summary of the data retrieved from the ESXi host (Host Data) and data found in the HCL (HCL Data) against multiple categories. Evaluation is done sequentially starting with Partner data and continuing with Model, CPU series, down to BIOS. On a mismatch between Host Data and HCL Data the evaluation process will stop, and a red exclamation symbol will be displayed to indicate a possible incompatibility. The data also provides other known/supported options if these are available from the HCL. Information collected from the Host will still be shown for all categories.
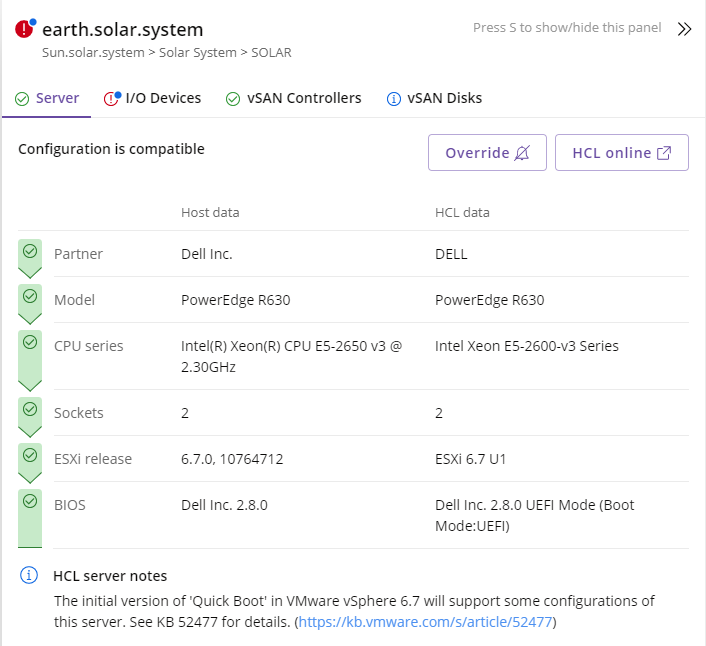
If you want to see detail directly from the VMware HCL webpage you can click on the button labelled HCL online which will open a new browser tab linked to the specific server selected (if an internet connection is not available a message will be displayed).
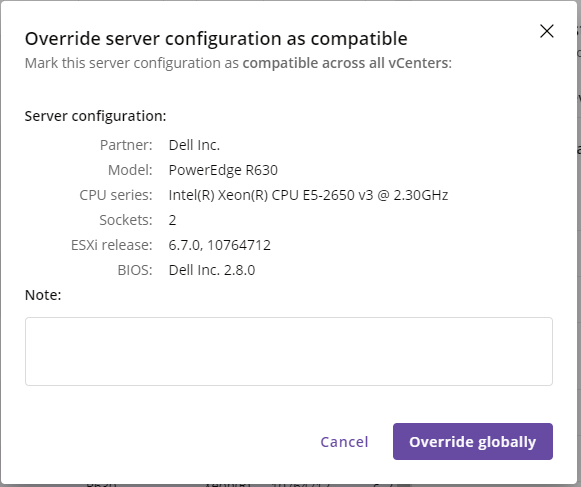
The override functionality provides the ability to enforce the result to any of the devices, to pass the evaluation criteria. Once the override has been applied, all the devices matching the same properties will inherit the new status. The device will be then marked as Compatible (Override applied)  .
.
I/O Devices
I/O Devices tab contains a list of all I/O devices present on the server selected. Compatibility states are shown using a green (compatible) or red (possibly incompatible) symbol. For each device, specific information about the PCI address and other technical IDs are shown. If you want to see the detail on the VMware HCL webpage you can click on the button  to open a new browser tab linked specifically for the device.
to open a new browser tab linked specifically for the device.
To expand a specific device to view its detail, click on the name or 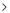 symbol. You will be shown evaluation results concerning the HCL Data. The evaluation sequence uses categories starting with IDs, Brand Name, Model, Device Type and continuing with ESXi Release and Driver, Firmware. If there is a mismatch between Host Data and HCL Data the evaluation will stop, showing a red symbol to indicate a possible incompatibility. You will also be shown known/supported options if these are available (information collected from the Host will still be shown for all categories).
symbol. You will be shown evaluation results concerning the HCL Data. The evaluation sequence uses categories starting with IDs, Brand Name, Model, Device Type and continuing with ESXi Release and Driver, Firmware. If there is a mismatch between Host Data and HCL Data the evaluation will stop, showing a red symbol to indicate a possible incompatibility. You will also be shown known/supported options if these are available (information collected from the Host will still be shown for all categories).
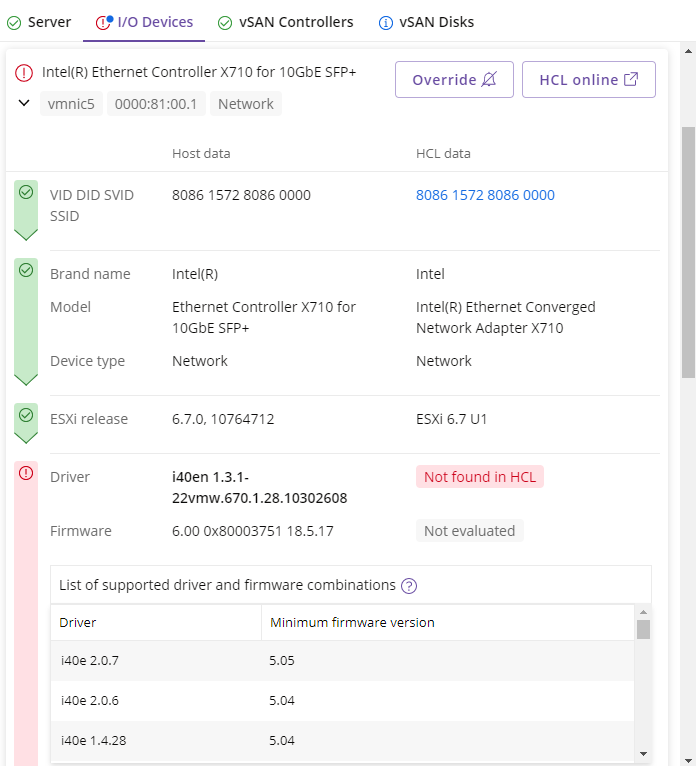
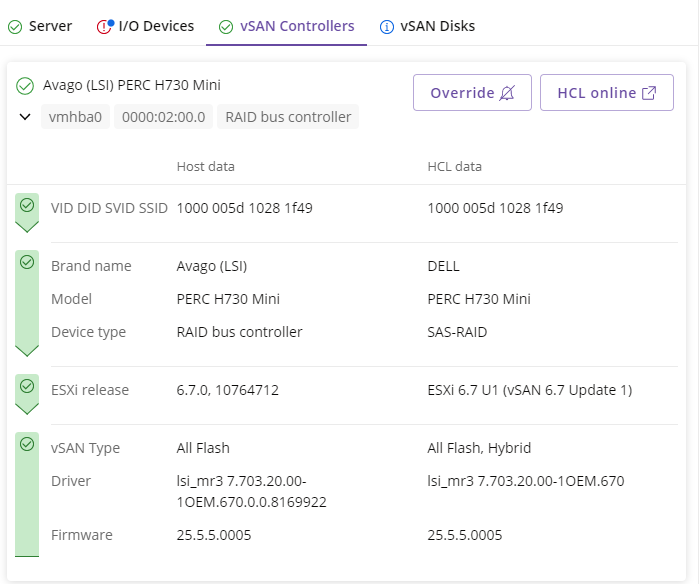
vSAN Controllers
This tab will be available only when vSAN is configured. Compatibility states are shown using a green (compatible) or red (possibly incompatible) symbol. For each controller, specific information about name, type and other technical IDs are shown. If you want to see the detail on the VMware HCL webpage you can click on the button  to open a new browser tab linked specifically for the device.
to open a new browser tab linked specifically for the device.
To expand a specific device to view its detail, click on the name or  symbol. You will be shown evaluation results concerning the HCL Data. The evaluation sequence uses categories starting with IDs, Brand Name, Model, Device Type and continuing with ESXi Release and vSAN Type, Driver, Firmware. If there is a mismatch between Host Data and HCL Data the evaluation will stop, showing a red symbol to indicate a possible incompatibility. You will also be shown known/supported options if these are available (information collected from the Host will still be shown for all categories).
symbol. You will be shown evaluation results concerning the HCL Data. The evaluation sequence uses categories starting with IDs, Brand Name, Model, Device Type and continuing with ESXi Release and vSAN Type, Driver, Firmware. If there is a mismatch between Host Data and HCL Data the evaluation will stop, showing a red symbol to indicate a possible incompatibility. You will also be shown known/supported options if these are available (information collected from the Host will still be shown for all categories).
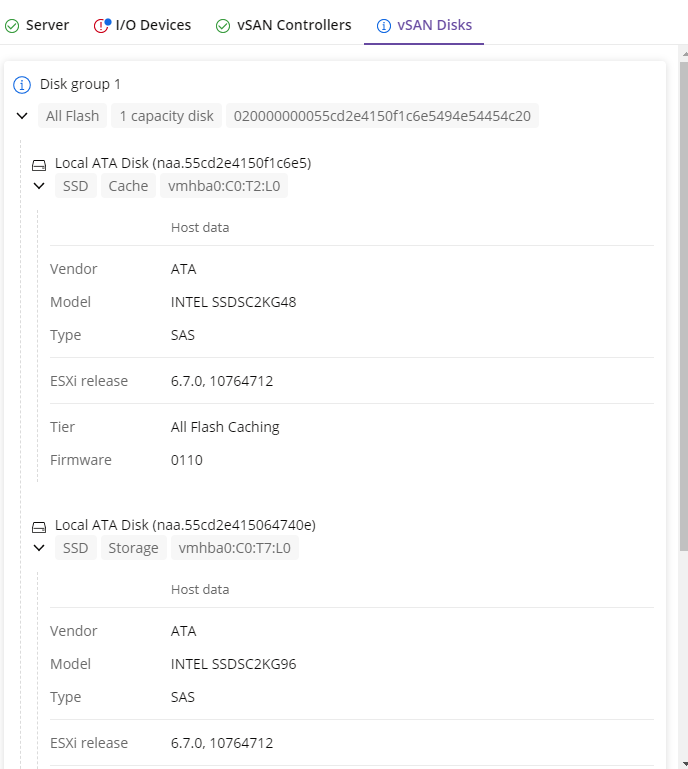
vSAN Disks
vSAN Disks are displayed without any compatibility evaluation and are providing informative data  about each group and its disks.
about each group and its disks.
On all detail tabs, the far right-hand side of each category contains a button showing a loud-speaker icon 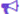 which appears on hover:
which appears on hover:
The button is available for both states – compatible or possibly incompatible and gives you the option to report an issue if a match was not made as expected, or a mismatch occurred. If an internet connection is available, clicking the loud-speaker icon will present a window showing the (anonymized) data collected. The button to send the data can then be used to submit. If an internet connection is not available, the window will provide steps to download the file and e-mail to the support team. We very much welcome any feedback.
Capacity Management
The Capacity Management feature shows overview of the compute resources utilization in a vSphere environment. With each analysis, Runecast Analyzer will store a snapshot of the capacity-related data, allowing you to view not only the most recent statistics, but also the historical values. Important metrics like CPU/Memory utilization and overcommitment are visualized to provide fast feedback for the health of each cluster in your environment. Multiple tooltips inside each widget show more details and the predefined thresholds for each sate - Optimal, Warning and Critical. The data grid below the widgets includes more information about the available and the allocated resources.
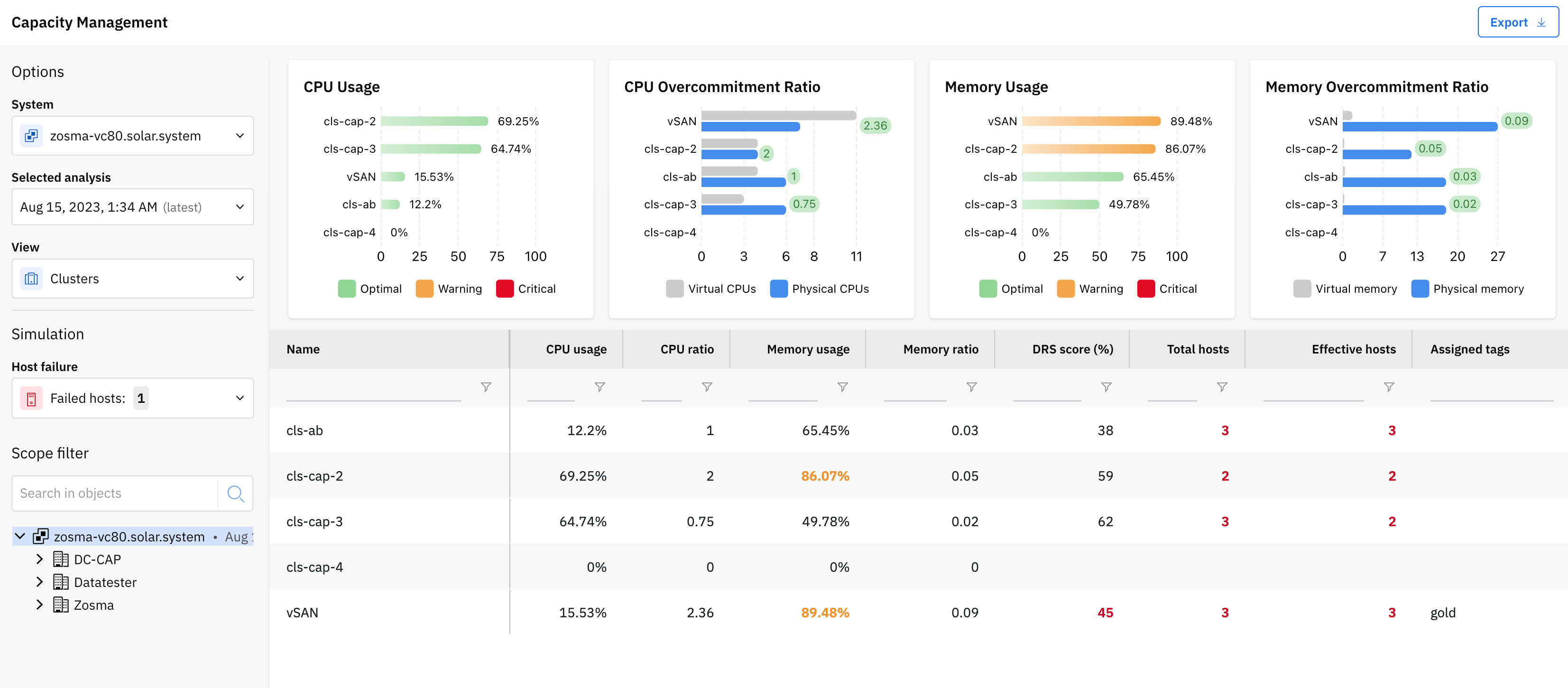
Additionally, from the left control panel, you can perform simulations against the current data: host failure or deployment of more VMs with certain virtual hardware configuration. Doing so will re-calculate the key metrics (CPU/Memory utilization and overcommitment) and provide an instant overview of what the resource utilization will be for each cluster in such a state.
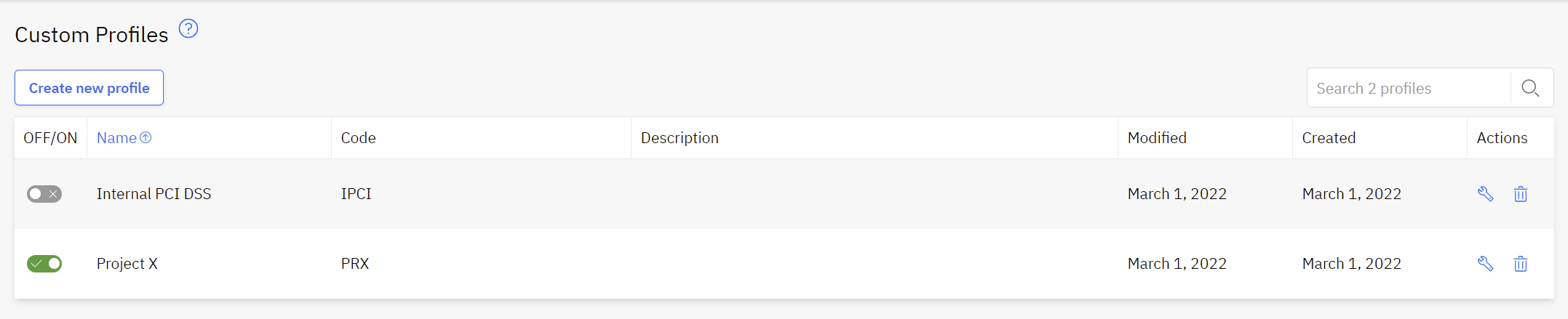
Custom Profiles
Allows you to create your own baseline by copying existing issues to a custom profile.
This feature will become available under the Configuration Analysis part after being enabled in Settings > Knowledge Profiles > Custom Profiles.
In the Profiles Management view you can either create a new profile or modify the existing ones.
To create a new profile press on the Create new profile button located in the top left corner. In the new pop-up window, add the Profile Name, the Code, and the Description. Press the Create a new profile button to generate the profile. The default profile status after creation is OFF. Switch the button to ON to enable the profile and to allow it to be displayed under the Custom Profiles section.
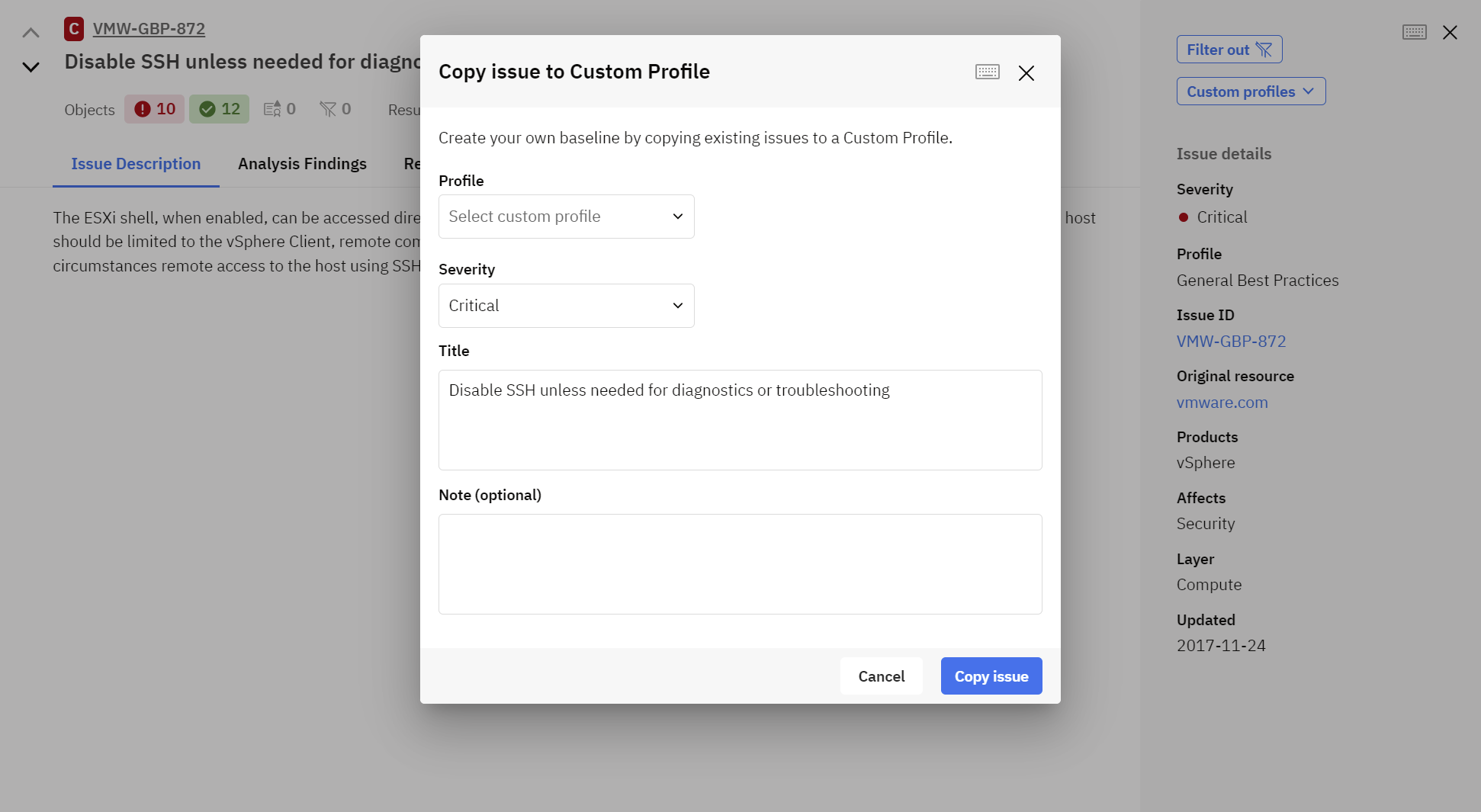
Adding any rule to custom profiles can be easily done by pressing the button Copy to Custom Profile, available under each rule once expanded. Before the rule being copied, you can select the desired Profile, change the Severity, provide a new Title and optionally add a Note. Press Copy issue to complete the action.
Both initial and custom rules are considered during the scan. If the initial rule is not needed anymore, it can be filtered out – see Filters.
Note
Just the configuration rules can be copied to Custom Profile. Exceptions are done by the log rules, marked as LOG on the Profile column in the Definition Database.